Investigating An Abusive Email
This year brought an unusual start to my Boxing Day morning.
As I do most mornings, I sat down with a coffee and checked email. This time, though, there was an email which really stood out, carrying the subject line kill yourself nazi
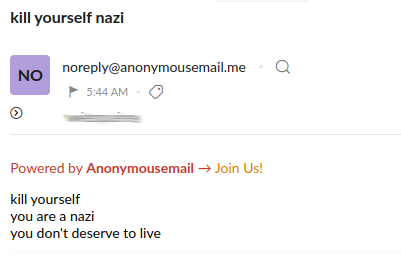
What a nice start to a bank holiday...
I've been on the internet for a long time now, so I'm quite used to receiving abuse along with sometimes concerted attempts to pwn my shit, but such events do still occasionally elicit some level of curiosity.
The word Nazi obviously has a very specific definition and it's really not a term that I'd expect to be being thrown at me.
Which raises the question: what might have motivated someone to choose that particular term?
It's more than possible that I've upset someone. For example, I recently reported someone sharing pictures of teens alongside some very questionable commentary, resulting in them losing their Mastodon account. But, there are about a million insults that are more likely as a result of that than the word "Nazi".
With my curiosity piqued and it being a bank holiday, I decided to spend a little time to see whether I could find any additional context.
This post details my investigation, as well as extracting some important general lessons from its findings.
Contents
- The Sending Service
- The Receiving Address
- Confirming the visitors IP address
- What prompted the mail?
- Summary
- Lessons
- Conclusion
The Sending Service
The email I received quite clearly states that it was sent via a service called anonymousemail.me, which is basically just a webform allowing the sending of arbitrary e-mails (with or without attachments) to whoever you choose:

I can't really think of any legitimate uses for this: it's a dream for abusers, spammers and phishers, but really not suited to many legitimate aims.
Like the majority of BadShitTM on the web, the service sits behind Cloudflare's CDN.
Once submitted, the mail is sent to the unfortunate recipient(s) by the service's mailservers which sit under a different 2nd level domain: eternalimpact.info
The servers are also used for incoming mail (presumably, to handle replies), and the following mail servers are listed in anonymousemail.me's MX record
anonymousemail.me mail is handled by 10 s7.eternalimpact.info.
anonymousemail.me mail is handled by 20 s8.eternalimpact.info.
anonymousemail.me mail is handled by 30 s6.eternalimpact.info.
The headers on the mail that I received show that it arrived from s7.eternalimpact.info.

As you'd expect from an anonymous mailing service, there's nothing in the received mail headers which directly help to identify the author of the mail (it's always worth looking though, mistakes do happen).
Receiving Address
In this case, the address that the mail was sent to provides additional information.
The address used is the one published as a contact address for this site and is only published in a single location: Contact Me (which is why I've blurred it in screenshots).
Logically then, the sender must have visted that page at some point.
Working on the assumption that I've written (or said) something which pissed the sender off, we'd expect to find that they checked my contact address around the time that the mail was sent. The contact me page isn't exactly high traffic, so their visit should stick out like a sore thumb.
I checked my analytics and sure enough there was a single visit to that page recorded overnight

The visit occurred just 58 seconds before the email landed in my mailbox, which quite tightly ties it to the sender.
Confirming the Visitor's IP address
With a known page-view to examine, it may be possible to identify the sender's IP address, depending on whether they were using other protections.
Most analytics systems collect and store a wealth of information about visitors connections and browsers. However, my PF Analytics system is specifically designed with data minimisation in mind and so does not unnecessarily collect identifying data (meaning no IPs, session identifiers etc etc).
However, this does not mean that the information cannot be obtained.
Because the visit was recent, it had not yet rotated out of my HTTP access logs (something which I also relied on when looking into the Cellebrite oddity back in April).
Sure enough, there was a log-line showing a request to /pages/about-me/contact-me.html

The blurred sections of this screenshot are IPs: the first is the IP of the responding edge node on my CDN, the second is the visitor's IPv4 address (this is the one we want).
Running a whois against the IP shows that it's part of a block used for Fiber-To-The-Home connections by Kazakhtelecom in Kazakhstan

The description also implies that block is used for dynamic IP allocations, but that cannot simply be taken at face value - it's not uncommon for the description not to be updated after a change of use.
Neither Shodan nor a quick nmap yield any results, supporting the idea that this is genuinely a consumer connection rather than an open proxy or a VPN endpoint.
It's easy to double-check whether the IP is that of a Tor exit node, using Tor's exit list service
dig +noall +comments +answer <ip>.dnsel.torproject.org
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 28141
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
The result is NXDOMAIN so this is not a Tor exit node.
Although it looks a lot like this is a consumer broadband connection, we still have information that can be used to try and build that confidence further.
The access log snippet above shows that the visitor had the user-agent of Firefox Mobile 108 on Android 11 (Red Velvet Cake).
Mozilla/5.0 (Android 11; Mobile; rv:108.0) Gecko/108.0 Firefox/108.0
So the request came from an Android device, or, something claiming to be one. Most anonymity browsers (such as Tor Browser Bundle) expose user-agents claiming to be on desktop devices.
The browser's timezone is one of the metrics that PFAnalytics does record, so we can also check whether that corroborates what we have so far

The values used for this metric are (IMO) a little weird. They're drawn directly from Javascript's getTimezoneOffset() which returns the number of minutes between the browser and UTC/GMT.
So, calling getTimezoneOffset in a browser configured to use UTC+2 will return -120 (because you subtract 120 minutes from the reported time to get to UTC time), conversely a browser running in New York (UTC-5) would return 300 because you need to add 300 minutes to the time to convert to UTC/GMT.
The Flux query which underpins that cell on my analytics dashboard then simply converts minutes to hours when querying metrics from InfluxDB
|> map(fn: (r) => ({ r with
// Response time ms -> seconds
_value: float(v: r.response_time) / 1000.0,
// Timezone mins -> hours
timezone: r.timezone / 60
}))
With a value of -6, we can see that the visitor's browser claimed to be operating in a timezone using UTC+6.
Kazakhstan spans two timezones: UTC+5 and UTC+6
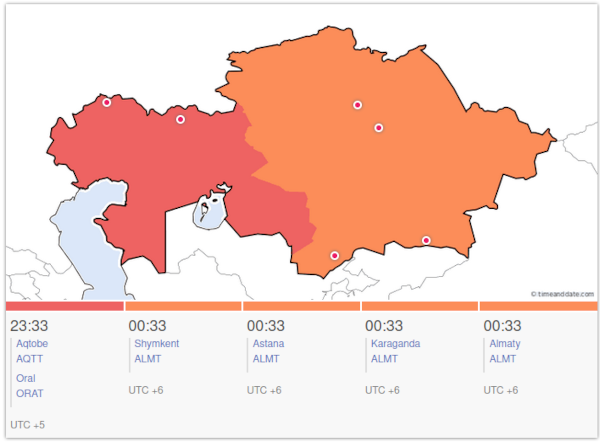
On it's own, this isn't definitive: parts of other countries (including Russia and China) are also in UTC+6. However, the other information that we have also points to Kazakhstan and we've not found any evidence to suggest that the visitor's connection was being proxied internationally.
To summarise, then
- The visitors IP belongs to a block owned by the largest Telecoms company in Kazakhstan
- The IP is in a block specifically labelled as being for FTTH (Fiber broadband)
- The IP does not appear to be a VPN endpoint, an open proxy, or a Tor exit node
- The user-agent is one associated with Firefox on an Android mobile device and not a UA commonly used by anonymity enhancing browsers
- The user's browser claims to be operating in
UTC+6 - Much of Kazakhstan is in
UTC+6
Whilst it's not a 100% certainty, we can be pretty confident that this is the visitor's genuine IP and that the requests came from an android device attached to a wireless network served by a fiber broadband connection.
It'd certainly be possible to try and look further into the author, but it's not necessary to do so to answer the question that we're actually trying to answer.
What Prompted The Mail?
The question we really want to answer is: why was this mail sent?
Was it simply some random act of shithousery, or have I inadvertantly caused gross offence somewhere? If the latter, then I'd probably want to find and at least try to correct.
Now that we've established some confidence in the visitor's IP as an identifier, we can use it to help look at their earlier activities: seeing what they were reading and how they came to be on my site might help to answer the question.
Other analytics systems allow easy viewing of a user's on-site movements, but one of the Fundamental PFAnalytics design criteria was that
The default behaviour should make it all but impossible to track user movements within a site
It's true that not honouring that fundamental principle would make thing like this easier but I won't implement detailed recording and retention of visitors activities just on the offchance that a need like this arises.
As before, because the activity was recent, we can use the HTTP access logs instead.
With a simple
grep <ip> access.log
The visitors requests are listed.
Amongst requests for various page requisites, we see this request

About 1 minute prior to hitting Contact Me, the visitor viewed my Stop The War post.
Written and published in March, the post lays out (in Russian and English) some of the atrocities that Russian forces were committing during their invasion of Ukraine. The post formed one part of a range of efforts to help push information into Russia using varying techniques (in fact, it's not even the only page used for that on my site).
It seems that I received the Nazi-Mail because the visitor objected to this page's mere existence.
They couldn't possibly have fully consumed its content: the logs show that they visited the page at 05:42:08, and moved to "About Me" just 40 seconds later, proceeding from there to Contact Me.
There are multiple videos on "Stop the War", the shortest of which is nearly 2 minutes long. So they couldn't possibly have consumed or considered the information that the page provides, even if they somehow managed to speed read the text.
The referrer section of the access log line shows that they had originally visited my recent post "Deciding Whether to Enable Automatic Post Deletion on Mastodon", so we can look up the log-line for that too:

The referrer section shows they arrived on that post via Google.
Sadly, it doesn't look like the visitor managed to read that blog post in full either, having requested the page just 19 seconds before they visited Stop The War. Presumably, they saw the red banner at the bottom of the page and immediately clicked it.

Putting it all together, we can build the following timeline
- Searched Google for something (we'll never know)
-
05:41:49: Followed a result to "Deciding Whether to Enable Automatic Post Deletion on Mastodon" -
05:42:08: Saw the red banner at the bottom and followed it to "Stop The War" -
05:42:47: Went to "About Me" -
05:43:02: Went to "Contact Me" -
05:44:55: Nasty-gram lands in my inbox
They landed on my site and then after just 58 seconds decided to send an anonymous mail telling me to kill myself.
Summary
As a TL:DR, we can summarise the above as follows
- I received an anonymous email calling me a Nazi and suggesting I kill myself
- That mail was sent using an anonymous mail service protected behind Cloudflare's CDN
- The mail was sent to an e-mail address that's only published in a single place
- Access logs show the author visiting that page to retrieve the address shortly before the mail was received
- Their IP, as well as metadata captured by analytics, strongly suggest they're in Kazakhstan
- Shortly before sending their hate-a-gram, the visitor landed on my "Stop The War" post (but is unlikely to have actually read it)
- Before that, they'd briefly been on "Deciding Whether to Enable Automatic Post Deletion on Mastodon" and presumably clicked the red banner to reach "Stop The War"
What we're looking at is a Vatnik (ватник): someone who has, unfortunately, swallowed The Kremlin's lies and propaganda so thoroughly that they'd rather send hate-mail than read even a part of the truth.
They had the forethought to send the mail anonymously, but seem not to have understood that the fact they'd just been directly interacting with my site fundamentally undermined any protections that they might implement around sending the email (the only "protection" at that point being to not send the mail).
It took far less time and effort to gather this information (I didn't even finish my coffee) than it has to write this post (I'm now several large Southern Comforts in, yippee).
Lessons
It's very easy, tempting even, to rail against the person. But, as much as I'd like to tell them to go fuck themselves, the mail and it's author are just a symptom of the problem.
It's clear that there's still work left to do in trying to get the truth of the war in Ukraine to those within the Kremlin's sphere of influence, including those in Kazakhstan.
I've previously had some (much more positive) interaction with users and networks in Kazakhstan, so have some understanding of the effort that their government puts into its attempts at controlling the flow of information (via Telcos). Reliably getting information in can be challenging at times (although far from impossible).
There will always be individuals who refuse to hear or see the truth, but this interaction is probably best viewed as an indicator that we're perhaps still not managing to push enough information to break Russia's false narratives. It's clear that the author of the email believes the Kremlin's claim that Russia invaded Ukraine in order to free it of Nazis. Although we might never convince this individual otherwise, any effort that it drives may still help others to see the truth.
What someone in Kazakhstan believes about the war likely matters far less than what someone in Russia believes (as limited as an individual Russian citizens power to stop the war might be, they still have more say in Russian affairs than a Kazakhstani). Getting the truth into countries like Kazakhstan, though, is still an important aspect of breaking the stranglehold that the Kremlin (and its various puppet governments) is attempting to maintain on information. The more widely the Kremlin's narrative is broken, the harder it is for the liars to try and reinforce themselves with more lies.
This incident also demonstrates that users really aren't very good at opsec.
The existence of the anonymous mailing service seems to have helped the mail's author develop a false sense of security. The author took and (presumably) felt empowered by precautions, whilst lacking sufficient understanding to realise that those precautions were nothing but theatre, offering no protection because they'd already been fatally undermined.
Side Note: we have the term "Dutch Courage" for drunken courage, so there has to be a better name for this than anonymous internet warrior syndrome.
Conclusion
The author of the email really has been a bit of a cockwomble, doing the online equivalent of putting a turd through the letterbox as they leave someone's house. It's unpleasant and the fact that they put gloves on doesn't do much to stop the perpetrator being identified, because they're the only person it could reasonably have been.
As with most online abuse, the email serves no purpose except to satiate the author's desire to send it. It provides no context, so
- can never hope to change the mind or behaviour of the recipient
- is extremely unlikely to achieve its stated aim (Kill yourself):
99.999999%of recipients are not going to kill themselves (that0.000001%, though, is part of why sending such a mail is despicable)
Sending hate over a topic you care about is an utterly pointless endeavour, it doesn't drive change and serves only to soothe the author with some false sense of valiance. If you genuinely care about something enough to want to see change, write convincing arguments, not pointless attacks.
In this case, it looks as though the author sent the mail because they objected to seeing (but not actually reading) a truthful description of Russia's invasion of Ukraine.
Their response was to send a hateful email, but only after browsing the site of the person they were attempting to abuse, crucially accessing the only page with the email address that they targeted on. This mistake meant that, despite their use of an anonymous mailing service, it was absolutely trivial to trace the author.
In some circumstances, the false sense of security offered by anonymous mailing services is potentially dangerous. Users who believe they're anonymous and protected sometimes find out, in the worst possible ways, that full anonymity is an extremely difficult aspiration to achieve.
I was only interested in determining why the mail might have been sent, but it's not beyond the realms of belief that others might not feel quite so restrained about investigating the author's meat-space identity in order to deliver some form of retribution.
I haven't reported this incident to the author's ISP.
Although the email is objectionable, the underlying issue is that the author lives under a repressive regime who controls the flow of information. It's also not really the authors fault that their authoritarian government maintains close ties with Moscow, itself a regime intent on spreading lies in support of Putin's dated and imperialistic ambitions (and so confident in success, that multiple media sources even accidentally declared victory early in the war).
And, of course, it's quite unlikely that the ISP would bother to act on a report anyway.
Fuck Cloudflare
Although I can't think of a single legitimate use for anonymouse.me, I've also not reported the service to Cloudflare because, frankly, I don't have any faith that Cloudflare would handle such a report responsibly.
- By default, Cloudflare shares your details with the operator of the service you're reporting
- Reports submitted to Cloudflare are subject to their Privacy Policy, which includes the potential for use for marketing reasons, as well as transfer of data outside of the EEA (CF don't define which categories reports actually fall under, so it has to be assumed they'll interpret the ambiguity to their own benefit)
Cloudflare's abuse approach can best be summarised as "not my problem guv". It's predicated on the idea that they're nothing but a dumb conduit and that the organisation hosting the origin needs to take responsibility instead.
This position has led to them responding to complaints by sending the complainants full contact details on to the service being complained about. Below is a screenshot showing a complaint, complete with the complainant's home address being published after being received by Kiwi Farms:
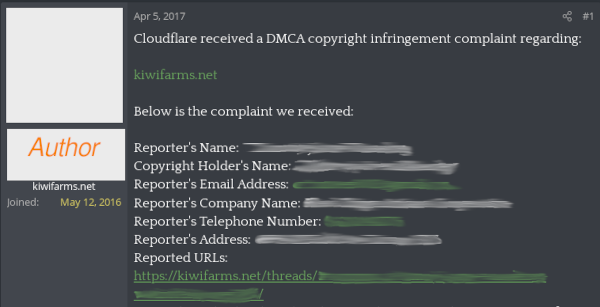
(I've redacted the content, as well as the author's profile)
Arguably, the "dumb conduit" argument only makes sense when arbitrary traffic transits a provider, rather than when the operator has contractual arrangements with the originator of the content that they're serving/carrying. Given that those arrangements exist, when a site's entire existence can only lead to issues, the question of whether Cloudflare should be serving that content at all should (but doesn't) arise.
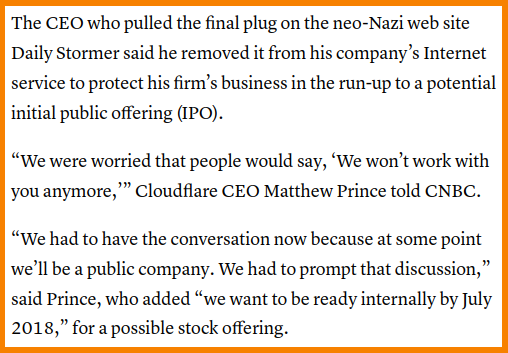
Cloudflare clearly have an extremely hostile view of abuse reports, imposing an incredibly high threshold on when they'll take action. They took months to ban a literal neo-Nazi website and later wrote of regret for that ban when considering dropping another customer.
Their CEO, Matthew Prince appears to have been quite content for Cloudflare to be serving Neo-Nazi content, protecting terrorists, serving forums used to announce and celebrate mass shootings, as well as harassment campaigns that are known to have led to suicides (each openly celebrated on said forum).
It seems that a change in direction happened only after things escalated into a perceived threat to CloudFlare's bottom line: profit before ethics FTW.
I've long been a strong supporter of net neutrality and opponent of censorship, especially attempts to force connectivity providers to exert control over the information transiting their network.
Cloudflare, though, is not simply a connectivity provider ferrying packets around, they're a TCP and SSL terminator with agency over who and what they will and won't serve (both downstream and upstream). They're not an ISP acting as a dumb conduit, they're a CDN, acting as hosting-provider-by-proxy, serving content for customers that they have a contractual relationship.
It's therefore reasonable to expect that Cloudflare exercise some degree of responsibility over who they do business with and it's entirely disingenous of them to hide behind many of the arguments that they've historically relied upon.
Making a commercial decision to putting profit before ethics and responsibility is entirely within their gift, but the very least that they can do is to be honest about what they're doing, and what the consequences of that are:

Negative headlines may impact Cloudflare's stock price, but each of the underlying stories represents a consequence of Cloudflare's (in)action, with the burden of that carried by families around the globe.
Cloudflare's stance is an area of intense debate, but whatever your views on it, it simply doesn't seem worth providing Cloudflare with the information they want alongside a report in this case. At best, they'll shrug and say "nah, don't give a fuck mate", but at worst they'll hand my details over to the operator of the service, potentially triggering a retaliatory harrassment campaign.
This really shouldn't need to be a consideration, a service provider that can't be trusted with abuse reports really shouldn't be in the privileged position of needing to receive them. So yeah, Fuck Cloudflare and the horse they rode in on.
The Final Word
Not everyone is able to shrug off abusive messages as easily as I am and, really, no-one should need to be.
As much as things like the Online Safety Bill might argue otherwise, the answer isn't to try and end anonymity on the Internet. As I've shown here (and in other posts), most users aren't nearly as anonymous as they think they are anyway.
It's important that root causes are identified so that they can be addressed. Some are exceptionally hard problems to solve, harder even than countering The Kremlin's continuous stream of lies, but until the underlying rot is fixed, abuse will find new cracks and crevices to seep through.
The volume of abuse sent under real names, on networks such as Facebook and LinkedIN, would suggest that the end of anonymity wouldn't achieve any positive difference, bringing only harm to those who rely on anonymity for their safety.
Not that it's likely to be seen, but to the person who started all this, I have 4 things to say
- Read some content online rather than relying on local news alone. Start with my post, or someone elses, but read something
- Stop calling people Nazis in support of a country committing War Crimes in Ukraine
- I agree with your general sentiment: Real Nazis can fuck right off
- Slava Ukraini, you vatnik motherfucker
