Stop Requiring Phone Numbers
I recently wrote about the need to observe the overall aims of GDPR when designing compliance into a system.
In that post, I wrote a little about my objections to the unnecessary collection of phone numbers, something that I've alluded to in past posts (also here (NSFW)) but never really laid out in much depth.
This post will lay out the issues inherent in collection and processing of phone numbers, as well as why those issues mean that that processing is (IMO) unnecessary, unjustified and needs to be replaced with better solutions.
A phone number is special
Amongst the myriad means of communication that humans use, phones are basically unique.
No matter what we're doing, a phone call (and to some extent, a SMS) always acts as an interruptor. If your phone rings, you're going to stop what you were doing and check it (even if only to then reject the call). Whatever chain of thought you had been pursuing is often lost in the process.
No matter how many emails you send, you're unlikely to wake someone during the night, but a phone-call will almost always elicit a tired hello?.

The interrupting nature of phones is, of course, hugely beneficial during an emergency, but significantly less pleasant when used for other purposes.
Although our phone number might not have changed, over the years, the way in which that number is used has changed.
Previously, a phone number was an identifier used for a single mode of communication - a phone call - numbers are now used for additional communication methods:
- As an identifier for services like Signal, Whatsapp and Telegram (all of which can be used not just for messaging, but to initiate encrypted voice calls)
- As an authenticator for various services. Some services uses SMS for 2 factor authentication, and some use a phone call - in either case, demonstrating proof-of-control over the number helps to authenticate you.
It's possible to write an entire article on the issues involved in having a single thing act as both an identifier and an authenticator, but I'll steer clear of that for the time being.
Minimal Access Controls
Most of us have very little control over who calls (and when). There's no negotiation involved in making a call, the caller dials when it suits them: If you picked up your phone and dialled a random number, you'd disturb a stranger.
We rely almost entirely on the fact that anyone wanting to contact us specifically is unlikely to stumble upon our number because we're one number in a vast pool.
But, once this obscurity fails to protect us, the only real defence we have against a number we don't recognise is the age-old tactic of call screening: waiting for the call to fall through to answerphone/voicemail and see who it was (and what they wanted).

Modern phones allow you to block numbers, but it's reactive and doesn't scale particularly well. You won't know to block a number until you've received a call from it, and you'll likely only block a very small set of numbers. Any caller with anything less than a sense of fair play will call from different numbers (or use number spoofing to achieve the same end) in order to get around blocks.
Honest marketing agencies can be defended against using things like the telephone preference service, but abuse continues to be an issue even amongst otherwise legitimate firms.
Of course, these mitigations are just for phone calls and SMS, but our number is also often used as an identifier on other networks, each of which with it's own issues. For example, Whatsapp spam is rife.
It is possible to implement extreme measures like enabling Do Not Disturb permanently so that your contact list acts as a whitelist. This does rather undermine the utility of the phone though and it only stops notifications. Your call log (and messaging inbox) will still be filled with noise and use of the phone will still be interrupted by the incoming call screen.
In practise, then, we have very little defense against any meaningful volume of unwanted contact attempts using a phone number. In some countries, you may even be paying for the "privilege" of receiving those nuisance calls and messages.
It's Not just marketing
We all hate marketing calls, but they're actually the best case scenario for misuse of our contact details.
Phone numbers are also used to target people with harassment, threats and abuse

Although apparently not in the above case, it's not uncommon for an abuser to spoof their victim's number when calling the police during a swatting attempt. Doing so helps to increase the Police's confidence in the report and, although some of the media mischaracterise it as a prank, swatting really should be considered akin to attempted murder.
Swatting attacks aren't just limited to gaming disputes (though deaths have occured there too) occur in a wide range of different situations
- A 16 year old used swatting as part of his campaign harassing multiple women.
- LAPD arrested a juvenile for swatting multiple celebrities
- A Tennessee man died of a massive heart attack when SWAT entered his home. He'd been targetted by someone who wanted his twitter handle
Because network providers sell customer location data someone who knows a phone number may also be able to track the phone's location, potentially helping an online dispute spill over into the real world. There's also a mechanism called Silent SMS which can be used to "ping" a phone - access to it is (theoretically) limited to Police and Security Services, but their record on this is less than stellar.
Swatting and stalking are clearly on the more extreme end of harassment, but a phone number can be used in a wide range of other ways:
- nuisance dialing (letting the phone ring a few times and then hanging up before repeating)
- silent/heavy breathing calls
- abusive text messages
- non-consenual sharing of pictures (including, but not limited to, dick pics)
- debt collection calls
- "For a good time call..." graffiti and classified ads placed under the owner's name
Although the law recognises that harassment comes in many forms, it's of limited use - even in extreme cases - if the harasser is in another jurisdiction. The law only provides protection if it can actually be applied to the source of the harassment, so whilst improvements in the law are welcome, it can only really be viewed as a defence of last resort.
We'll look a little more at a specific harassment campaign later in this post.
A phone number is also useful to fraudsters.
Combining a number with other information (whether from the same, or another, leak) allows them to build a more credible story to convince a mark with. As an easy example: the "bank" ('onest, guv) calls your nan and reads out her NI/SS number to "verify" themselves, before asking her to provide sensitive information to "verify herself".
If you are really unfortunate, the contact may not be deliberately directed at you.
Once a number is public, there's very little discrimination over who actually owns it.
This effect was highlighted last year when a Korean man received 4,000 calls a day after his number was shown in the series Squid Game. There was no malicious intent, nor were viewers in any way encouraged to call the number, but the result was that the number the owner had used for 10 years suddenly started to constantly receive calls, messages and photos.
Because phone numbers are recycled there is chance that any new phone number we get might have been leaked at some point in the past (although probably not in a popular TV drama).
How numbers get disclosed
Now that we've got a high-level view of the issues that a phone number can enable, we need to look at how numbers get out into the wild.
Just occasionally, a user might unthinkingly publish their own number, but they are very much in the minority. It's far more common, unfortunately, that numbers are misused or lost by organisations which had a seemingly valid reason to hold them:
- Twitter misused numbers provided for SMS 2FA in advertising activities
- T-Mobile data breach impacts ~50 million customers
- Phone numbers for 533 million facebook users leaked on hacking forum
- Phone number of 5.4m Twitter users leaked by vulnerability in it's auth process
- Storehub leaks a million records (inc phone numbers) from unsecured Elastisearch server
In just six bulletpoints we're talking about more than 589 million records, with all but one of those breaches occurring in the last two years.
As high as that number might seem, it's small fry: in July a database containing the details (inc phone numbers) of over a billion Chinese citizens was put up for sale, having allegedly been stolen from the Shanghai Police.
A billion records, lost onto the net, just like that...

The majority of organisations listed here have access to skillsets and finances which should mean that they're less susceptible than most to data breaches. Yet, breaches continue to happen.
It's rarely a question of if instead one of when a compromise will occur.
Once contact details are out there, there's a risk that they may be misused years later, particularly if the owner is unaware of the compromise.
Why customers provide numbers
The examples listed above have something in common, because each could claim it had a legitimate reason for holding user's phone numbers:
- Facebook and Twitter collect(ed) numbers to help secure accounts, by using SMS as a second factor, as well as to allow users to find other users via their phone number.
- Storehub's collection of numbers will have allowed vendors to provide despatch and delivery notifications to customers.
It's not at all uncommon that these are used as a justification. In fact, just this week, Ebay provided a similar justification in my discussion with them about their processing of my number:
* Restoring account access by sending a one-time password via
SMS to a registered telephone number.
* Customer support needs to contact a user directly to prevent
damages in case of a security risk for a user account.
* Fraud prevention checks to protect users and the eBay platform
against money laundering.
* Protecting the eBay platform, buyers, and sellers acting on
the platform which provides a safe and secure marketplace.
E-commerce outfits also often use SMS to keep customers informed about the state of their order, sending delivery time estimates etc.
Whilst this, undoubtedly, is useful information, it could equally be delivered via e-mail - a method which wouldn't result in me being woken up at 7am on a Saturday by the sound of Holly saying "This is not a daffodil"
I cannot be the only person who's been woken early by a text that reads
Your driver is on the way. Go to order details for more information
Even though the delivery isn't due (and won't arrive) until several hours later. Knowing that your order is en route is a useful service, but being disturbed by a notification hours ahead of time is a nuisance.
Phone Number as an Authenticator
It's not uncommon for a phone number to be used as an authenticator, with codes being sent out via SMS as part of a SMS 2FA based scheme.
However, there are a number of less invasive alternatives which can be used to help protect accounts:
- TOTP (Authy / Google Authenticator / Microsoft Authenticator etc)
- U2F / WebAuthn / FIDO
- Yubico Yubikeys
Phone based authentication is cheap and easy to implement but, where alternatives are available, it's use is recommended against by NCSC
SMS is not the most secure type of MFA, but still offers
a huge advantage over not using any MFA. Any multi-factor
authentication is better than not having it at all.
However, if there are alternatives available that will
work for your use case, we recommend you use these
instead of SMS.
Although SMS/Phone based authentication uses an out-of-band communications channel, it's an unsecured channel and is vulnerable to attacks including
SS7 exploitation requires a more advanced attacker, and Stingrays are (in theory) confined to law enforcement usage, but the first two are inexpensive and require little sophistication to pull off.
This means that any authentication sent via the phone network can not and should not be strongly relied upon.
This is problematic even in services which support more effective methods but that also require that you configure phone based authentication (Twitter used to be one of those). The stronger protection is undermined by the attacker's ability to try and compromise phone-based-auth instead, breaking the weakest link in the chain.
If an authentication method cannot be relied upon and risks undermining other methods, why implement it?
Accessibility
Not everyone can use a phone for a range of reasons:
- disability
- lack of reliable phone signal
- working/visiting an area where mobiles are prohibited
- dead battery
- simply don't have a mobile phone
This is something that the Financial Conduct Authority recognises in it's guidance for implementing Strong Customer Authentication (2FA by another name):

A TOTP based solution doesn't require that the user be in range of a mobile network, and U2F/FIDO can be used in a wide range of devices, allowing devices to be created/adapted to suit a particular user's needs.
The Importance of Balance
Although it's sometimes about easing support costs/overheads, the collection of phone numbers often occurs in order to help mitigate the risk of account compromise.
It's a laudible aim, but fails to take a holistic view: the user's account on that specific service is better protected, but at the cost of onboarding additional contact details (the phone number), increasing the risk of those details leaking and exposing the user to issues ranging from unwanted marketing to deadly harassment and stalking.
To put it another way: the user's personal contact information is used to protect the service but a flaw in that service may lead to that contact information becoming publicly accessible.
History shows that those flaws do happen, even in companies with near-infinite budgets.
Currently, the balance is very much in the favour of the service provider: users provide contact information, which helps the service protect the value of their business by ensuring a "safe and secure" environment for users (who, admittedly, also derive some benefit from that environment).
For example, I very rarely use Ebay and probably average 2 purchases a year. But the burden (on the service provider) and risk (to me) of using SMS 2FA remains the same as if I were logging in daily.
Ebay need to protect my number 24 hours a day, 365.25 days a year. If they screw up, just the once (and they have in the past), then my contact information potentially ends up published on the open internet.
The burden of responsibility might fall on the service provider, but the risk and the consequences are carried entirely by the user.

A more balanced relationship would involve use of solutions which didn't carry such serious repercussions, and ideally wouldn't ask a user to provide additional personal information in order to better protect the information that the service already holds.
Insider Threat
The risk which companies must defend against does not always come from external sources, sometimes breaches and misuse occur from within the company.
Ebay, should be acutely aware of the harm that harassment campaigns can do, being less than a year out of a scandal involving a campaign of harassment orchestrated by members of their senior staff.
In 2021, their security boss was convicted for harassing a couple who ran a newsletter critical of ebay. He was the last of seven former Ebay employees (including two executives) to be charged for their part in the harassment campaign.

As well as being subjected to a barrage of abusive tweets and messages, the victims
- Were sent deliveries of unpleasant and embarrasing items (including live insects, a fetal pig, and the book "Grief Diaries: Surviving the Loss of a Spouse")
- Had a funeral wreath delivered
- Had Hustler: Barely Legal delivered, in their names, to three of their neighbours addresses
- Had their property vandalised
- Were followed by the harassers, who'd travelled across the country and rented a black van for the purpose
- Were doxxed on twitter
- Had their email addresses subscribed to dozens of email newsletters
- Received a voicemail in response to their purported interest in opening a sex toys franchise
- Had their home address listed in a classified advertisement seeking swingers and others "looking for a good time"
- Had their home address listed in a "Everything must go" advertisement on Craiglist, as well as a second advert looking for "swingers and singles"
The affadavit makes clear that the harassers had intended to do much more (including attaching a GPS tracker to the couple's car), but became aware that the Police were running surveillance and so scaled back their ambitions (though they continued their harassment).
For their part, Ebay ran an investigation and fired the employees.
When we provide personal data to a company, we need to trust that they can protect it not just from external threats, but also from internal ones. The only way to be sure that an insider cannot access our phone number is not to provide it in the first place.
Ebay cannot function without our home addresses, but given their recent experience you'd have hoped they would have paused for thought before requiring the provision of additional contact details.
Convenience
There is an argument that phone number based solutions are convenient for users: they don't need an app or a dongle, all that's needed is a device capable of receiving SMS or calls.
It could equally be argued, though, that using a single password across all services is convenient. It's generally accepted that password re-use is a very bad idea and is strongly discouraged as a result.
Convenience is important, but it's by no means a trump card - something being convenient should not override all other concerns, especially if it means collecting additional identifying data like phone numbers.
By all means, offer a convenient option, but don't make it the only option in the belief that conveniene absolves you of the flaws in the implementation you've chosen.
Good Design Ethos
When designing things, we often question what the best way to achieve an end goal is: we could build x from scratch, but is there a turn-key solution we can use or adapt?
The same should be true here.
Using phone based communication to protect accounts is a solution, but it's often far from the best option
- TOTP doesn't require communication over an insecure second band
- U2F/FIDO supports a wide range of devices providing better accessibility
- Neither of the above are impacted by a break in mobile coverage
- Neither provide a means of contacting the user in the event of of a breach
- Open Source Solutions exist for TOTP/U2F/FIDO to codebases written in a wide range of languages
- Email is significantly less intrusive as a communications medium
- Nowadays, SMS based auth is probably not even the cheapest solution
There's nothing to prevent phone based communication being offered to users as an option, but in any well designed system it should be just that: an option.
In my earlier post, I argued that the principles of data protection by design and by default apply, but there's more to this than simple GDPR compliance.
Fundamentally, software design is about finding the most effective and efficient way to implement requirements and it's hard to envisage many scenarios where phone based communication is the correct answer.
Of the companies we've looked at in this post, I'd argue that only T-Mobile had a truly valid reason for storing phone numbers: they're a network provider, it's kind of their wheelhouse (although they seem to have decided they're in the business of selling customer data on).
All of the other uses-cases could have been achieved through less intrusive means. Had those companies used implementations that didn't involve storing a phone number, those numbers would not have been included in the subsequent leaks.
Conclusion
A phone number provides a means to contact us not just via voice call, but via an ever growing variety of means including SMS, Whatsapp, Signal and Telegram. A phone acts as an interruptor by default: When a phone rings, we stop what we're doing in order to check it, making it a uniquely intrusive means of communication.
There are a range of reasons we might be asked (or even required) to provide a phone number: companies tell us that it helps to protect our accounts, remain informed about our orders, or find friends on a social network. Many of those aims, though, can be achieved using less intrusive means.
A company holding your data needs to protect it 24/7 from both internal and external threats.
Unsurprisingly, compromises happen, even to the most valuable companies in the world, and personal details find their way out onto the net in their millions, being sold onto whoever is willing to pay for them.
A phone number is a powerful tool in the hands of a harasser, with some being harassed in clearly stated attempts to drive them to suicide, unfortunately suicides as the result of harrassment are not uncommon.
The worst forms of harassment are extremely severe and often long lived, but deliberate harassment is not the only risk that users are exposed to if their phone number is leaked. Being able to link a phone number to an identity helps increase the chances of a successful scam as well as providing (slightly) more value to spammers.
We have no meaningful way of controlling who calls or messages our number, and no real way to filter based on content, especially if the unwanted communications originates from a vast range of numbers (rendering local blocking useless).
The only way to be sure that a product cannot leak a user's phone number (or any other bit of data) is not to collect it in the first place.
Long ago, we realised the danger of storing passwords in plaintext and (although still too common) it's no longer considered an acceptable thing to do.
I hope that one day the same might be true of requiring and storing phone numbers when not absolutely necessary.
Reliance on phone numbers as an authentication vector really needs to end sooner rather than later - more effective alternatives have been available on the market for years, and can trivially be implemented using a range of opensource libraries:
- pyotp / py_webauthn
- java-totp / webauthn4j
- otp for Go / go-webauthn
- otp for NodeJS / webauthn for NodeJS
- otp for PHP / webauthn for PHP
Although we're not there yet, requiring phone numbers should already be considered unacceptable: we've known for years that the forced collection of phone numbers is building an enormous threat to user's safety and security.
Unfortunately, companies are still rolling out new projects which require them, including those who should really know better.
Update
Although not specifically just about phone numbers, there's an interesting thread starting up on the Cryptography mailing list about how best to protect Data in Use
One very powerful technique for securing Data in Use is to reduce the amount of tate in Use to the absolute bare minimum. So often we see breaches of databases containing PII, names, addresses, social security numbers, credit cards. And only very rarely is this PII actually required by the application itself.
Twilio has also declared a breach that occurred after some of it's staff received spear-phishing SMS messages to their mobile numbers. The report notes that the attackers were able to use other sources to match employee names to their phone numbers.
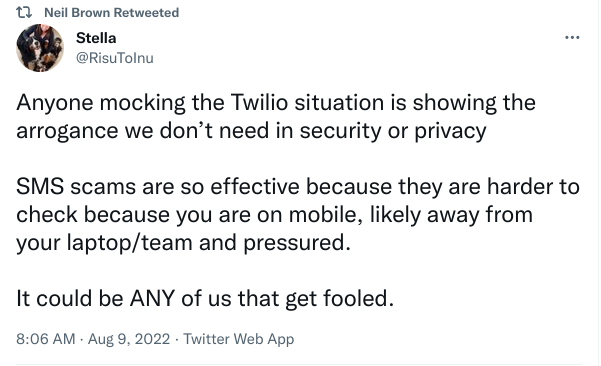
When you collect a user's number unnecessarily, it's not just them that you may putting at risk - a leak from your service may well help an attacker target a user's future employer.
That compromise, of course, has a knock-on effect. As a result of the Twilio breach, Signal users have been impacted, and the attackers may have accessed phone numbers and registration codes for 1900 Signal Users.
Update Dec 2022
As an additional kicker, Telcos are now reportedly attempting to shrug off any liability that they might have as the result of their staff being social engineered during sim-swapping attacks.

If you use your phone as an authentication vector, in AT&T's view, you get to shoulder the consequences "even if the damage results from the ordinary negligence of our installer or other representative".
Trusting authentication to a vendor who won't even take responsibility for their own negligence does not feel like a wise choice.
At the other end of the spectrum (see what I did there), Facebook say that it's the phone companies fault if accounts are hijacked as the result of number recycling.