Don't Use Web2Tor / Tor2Web (especially Onion.cab)
Web2Tor and Tor2Web are reverse proxies which allows clearnet users to access Tor Onion Sites (AKA Hidden Services), and there are a variety of services available online (such as onion.to, onion.cab, onion.city, onion.direct, onion.dog and onion.ws) running this service.
This post details why using these is, at best, a bad idea (and at worst, downright unsafe), as well as detailing some of the changes I'm making to the site to help discourage use of these services.
What is Web2Tor
Web2Tor exists so that users can access Onion services without using Tor. That's pretty much all there is to it, it listens on port 80 (or 443) on a clearnet server, and then proxies requests, via Tor, to the user's selected hidden service.
Why is it bad for the user?
When using Tor to connect to a hidden service (such as 6zdgh5a5e6zpchdz.onion, facebookcorewwwi.onion or e26whn2524322mkxb3cbyk27ev2ihhq2biz35hty7gzgsyrwrygq27yd.onion) your connection is protected by end-to-end encryption between your Tor client and the hidden service.
When you connect via Web2Tor, the Web2Tor instance sits between you and the hidden service, occupying a very privileged position that not only allows it to see what you're doing, but also to modify and inject content (see below for an example of that).
More than a few of these services serve content via plain HTTP, so your browsing activities are visible on the wire, but even where that isn't the case, because of the way Web2Tor works, you will still disclose the hidden service you're visiting to a wider audience. When you try and access 6zdgh5a5e6zpchdz.onion.cab, your system sends out a DNS query for that name, meaning that your ISP (and others) can see the hidden service you intend on visiting.
Others on the route between you and the Web2Tor instance can also see which Hidden service you're trying to access. Even if the Web2Tor instance is using HTTPS (not all do), the domain you're trying to visit is included within your browser's SSL handshake (known as the Server Name Identification extension).
So, by connecting to a hidden service via a Web2Tor instance, not only have you given a third-party opportunity to interfere with your connection, you've also announced which hidden service you're visiting to a much wider and unknown audience.
Content Injection
Some Web2Tor services, such as onion.cab and onion.ws, have some pretty bad habits, including playing fast and loose with your privacy.
For example, when accessing https://6zdgh5a5e6zpchdz.onion.cab/, the onion.cab service injects (piwik) Analytics code into the page:
var _paq = _paq || [];
_paq.push(["setCookieDomain", "*.onion.cab"]);
_paq.push(["trackPageView"]);
_paq.push(["enableLinkTracking"]);
_paq.push(["setDomains","*.onion.cab"]);
(function() {
var u=(("https:" == document.location.protocol) ? "https" : "http") + "://onion.cab/";
_paq.push(["setTrackerUrl", u+"pwk.php"]);
_paq.push(["setSiteId", "4"]);
var d=document, g=d.createElement("script"), s=d.getElementsByTagName("script")[0]; g.type="text/javascript";
g.defer=true; g.async=true; g.src=u+"pwk.php"; s.parentNode.insertBefore(g,s);
})();So, straight off the bat, we know there's a high chance they're keeping a record that your IP accessed specific pages on a specific .onion at a specific time. Not to mention that they're now running code on your browser that the original website author knows nothing about.
This Analytics code results in the explicit submission of some data into the analytics system
https://onion.cab/pwk.php?action_name=BenTasker.co.uk%20-%20The%20Home%20of%20Ben%20Tasker%20- %20www.bentasker.co.uk&idsite=4&rec=1&r=031912&h=18&m=3&s=38& url=https%3A%2F%2F6zdgh5a5e6zpchdz.onion.cab%2F& urlref=https%3A%2F%2F6zdgh5a5e6zpchdz.onion.cab%2F&_id=e3b76eefc37a7920& _idts=1481997157&_idvc=3&_idn=0&_refts=1488650352&_viewts=1488650352& _ref=https%3A%2F%2Fwww.google.co.uk%2F&send_image=1&pdf=1&qt=0& realp=0&wma=0&dir=0&fla=0&java=0&gears=0&ag=0&cookie=1 &res=1280x1024>_ms=1203
Within that long query string, amongst others, are
- Title of the page you're viewing
- An id for the site
- The time you made the request
- The exact URL you were viewing
- The page that referred you to that url
- Details of which plugins you have installed
- Whether cookies are enabled
- Your screen resolution
- A unique ID for you
More than a few of those should give cause for serious concern.
They also set various cookies (including the oddly named onion_cab_iKnowShit) , which can be used to track you across hidden services (so long as you're accessing via onion.cab), even if your home IP changes. In this instance, it's a self-hosted Piwik install, but it could just as easily have been Google Analytics (in fact, onion.ws injects code for Google Tag Manager).
And, just in case you've got Javascript disabled, there's also an "image" embedded within noscript tags to capture a subset of that information anyway.
<noscript>
<img src="https://onion.cab/pwk.php?idsite=4&rec=1" style="border:0" alt="" />
</noscript>Just to top it all off, they also rewrite various link and image anchors, which depending on what's rewritten may render the site broken and unusable anyway.
Always Go Direct
As we've seen, by using sites such as onion.cab, you're giving an unknown third party a lot of power.
They can inject content into the site, completely change the content you wanted to read, and (if you use them too much) can trivially track you across hidden services. All of which, pretty much undermine the usual reasons for using a hidden service in the first place.
If you're using Tor Browser Bundle to access an onion.cab site, then you're needlessly forsaking a lot of the protection you would otherwise have had (given that TBB can access them direct). If you're using a browser without Tor, you're still at risk.
Especially where the hidden service is multihomed, always use an official endpoint, which means
- https://www.bentasker.co.uk or http://6zdgh5a5e6zpchdz.onion/
- https://www.facebook.com or https://facebookcorewwwi.onion/
There might be times and occasions when using Web2Tor is justified, but unless you understand the ramifications of doing so, you put yourself at un-necessary risk.
Blocking Access
Ever since the inception of a Hidden Service endpoint for this site, I've blocked known Tor2Web instances (for the reasons above, as well as to avoid incurring a duplicate content penalty in Google's indexes). Unfortunately, not every Tor2Web operator is onboard with disclosing that it's a Tor2Web instance, and so not every instance adds the X-Tor2Web header.
For those that do (such as onion.to) users will see the following error message

For those instances that don't include an X-Tor2Web header, I'm in the process of making some changes in order to mitigate further
- The site will soon present a warning to the user if it's accessed through any but the official domains
- For those using my adblock lists, I've explicitly blocked
onion.cab's Piwik instance. - An
onion.cabhandler is going to be added to the site to prevent the Piwik includes for anyone who's adblocker doesn't catch it - The handler will also undo some of their anchor rewrites
Which ultimately results in a warning like the following being displayed to the user
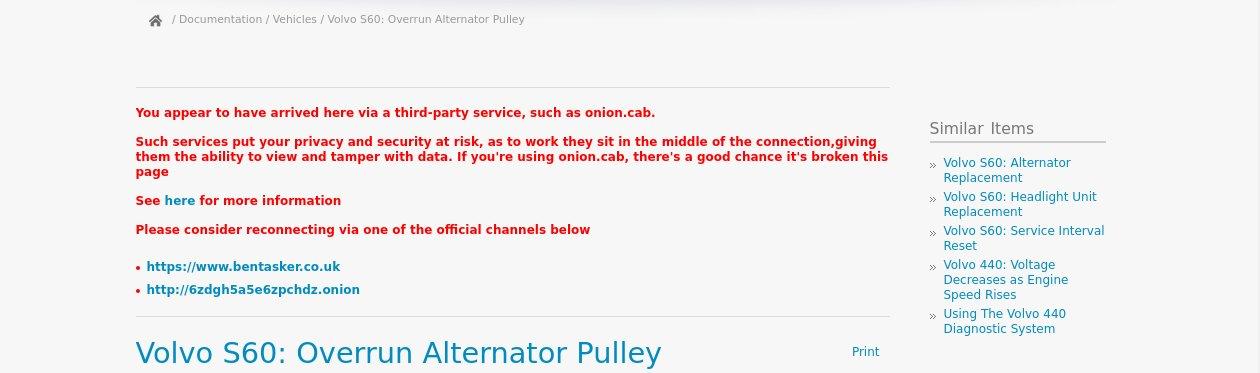
Although onion.cab is firmly on my shit-list, the above should help with other similar services, and I'm not intending to expend any effort on watching onion.cab to update my counter-measures. They're a Man in The Middle, so could quite easily strip anything I add.
Conclusion
Using a Web2Tor instance seems like an easy solution for accessing Hidden Services, but in doing so, you're introducing a privileged third party into the loop. Some of whom aren't always behaving as they should (whatever their actual intentions might be).
On Reddit, people sometimes suggest using these services as a troubleshooting step. It's not a good idea. If you can't access a hidden service with the Tor Browser, you've either messed up the configuration, or the hidden service is down (which is far from unusual). Using web2tor means giving up a lot of control over your anonymity.
Aside from the details above, there're other considerations to be made too. Using Tor2Web allows user/onion correlation, and allows these services to enumerate valid onions (which some, apparently, then sell on). Onion.cab publishes a list here - https://onion.cab/list.php
Wherever possible, always use an official endpoint. That way you only have to worry about trusting the site admin, rather than adding another stranger into the mix.