Security Flaw in the Computrend Powergrid 902 Adaptor
This article was originally published at Benscomputer.no-ip.org in 2009
OK, so I was playing around testing NetManage when I discovered something of a security flaw in the ComTrend Powerline 902 Adaptors I use when I want to use a laptop somewhere that I haven't got a Wired Connection.
Quite how serious it is is hard to say, in theory an attacker would have to already have access to your network in order to exploit it, but I suppose there is a risk that they could risk a more obvious attack once in order to glean this information. It also calls into question quite why ComTrend would bother to Password protect the Advanced Information page, but none of the ones below it.
My Biggest concern is that BT have been shipping these things with BT Vision, and if there is a bigger attack vector than I'm presuming then it could affect a lot of people. None the less there is no way they will listen to me if I try to raise the issue, so here we go.
If you point your Webbrowser at one of the adaptors (You're not going to have less than two after all), you should be prompted to enter a password;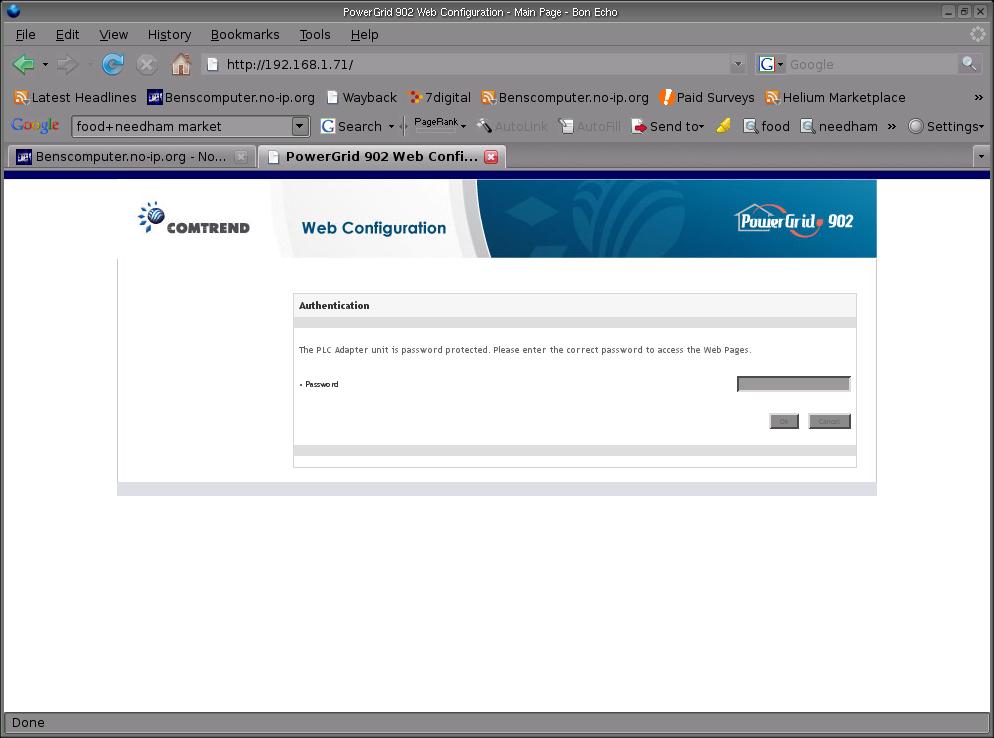
If you get the password wrong, you get Access Denied
It's all good so far, but now try changing the URL manually to http://IP.ADDRESS/mac.htm, as you can see below the adaptor will quite happily let an unauthenticated user view the encryption key it uses for its transmissions 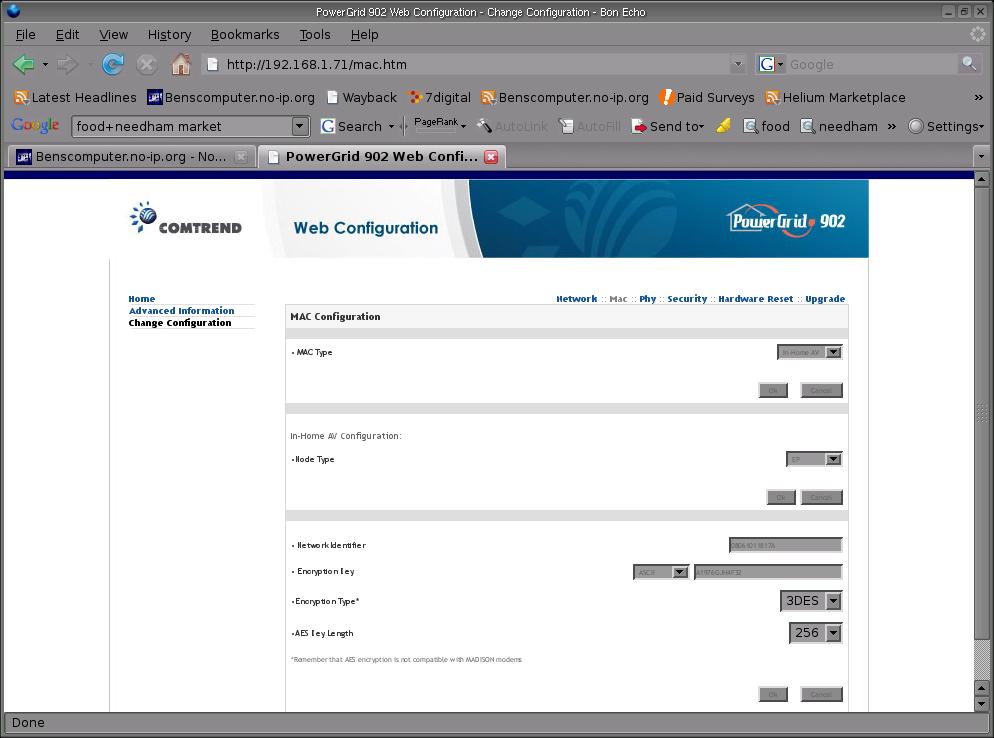
In Fact you can also view it changing the URL to point to info_mac.htm.
Now try clicking the Advanced Information or Configuration link, it will chuck you out. The Information on these pages is far less sensitive, yet it's been protected.
In reality, even if someone did get hold of your encryption key they would need to plug into a mains socket reasonably close to your house/office, but your neighbours could probably make use of it.
As I mentioned before an attacker would need to gain access to your network before they could view this information, and the adapator won't let an unauthenticated user change anything, but a poorly configured NAT router could potentially stick one of these adaptors in your DMZ, or enable port forwarding to it.
I haven't checked to see if the adaptor will allow you to log in from an I.P. outside it's own subnet, but I'm guessing it probably does. Make your own mind up about hwo big a threat this really poses, but keeping in mind a lot of these things have been shipped it does seem worrying that the system has such an obvious flaw.
A quick note for anyone who lives near me, I've already changed the encryption key, and very rarely use the adaptors anyway. Just to save you some time.
I'm off to Google to see if I can find any publicly accessible adaptors!
UPDATE: I figured I'd take a proper look at the security of the adaptors, how easy is it to run remote code on them etc. In other words is it possible to load some form of Network Sniffer/Cracker on them, exactly what Algorithm is used in the encryption etc. As a starting point, I decided to point Nessus in the direction of one of my adaptors.
It found an Etherleak vulnerability, Now depending on the type of network you are running, this is either inconsequential, or really quite bad. Potentially, it could also possibly be of use if the Padded Data you get back is an adaptor on someone else's network trying to connect to yours. Presumably as part of a connect request it would send a recognisable header encrypted with its own key, if you know what this header is, you may even get as far as deciphering the key.
If you are running a corporate network with these things, it could also potentially be bad, though given the nature of the devices, they shouldn't see any more than you can, and the attacker would already be on your network.
Still, these devices are really starting to stink of cheaply made crap.
UPDATE 2: Sorry, got my dunces hat on today. Mentioned earlier that I wanted to see what Algorithm the devices use for encryption, it actually says in the screenshot that they use 3DES Encryption
