Recovering files from SD Cards and How to protect yourself
I was working on writing this up anyway, but as the UK Government's lawyers have recommend weakening protections around Police's ability to search phones, I thought today might be a good day to get a post up about the protection of content on SD cards.
I never seem to have a micro-SD card to hand when I need one, they're generally all either in use or missing.
I tinker with Raspberry Pi's quite a lot, so, I ordered a job lot of used micro-SDs from ebay so that I could just have a pot of them sat there.
I thought it'd be interesting to see how many of the cards had been securely erased, and by extension what nature of material could wind up being restored off them.
Part of the point in this exercise was also to bring my knowledge of recovery back up to date, although I've done it from time to time - I've not really written anything on it since 2010 (An easier method for recovering deleted files on Linux, and the much earlier Howto recovered deleted filenodes on an ext2 filesystem - yes, that old that it's ext2!).
In this post I'll walk through how I (trivially) recovered data, as well as an overview of what I recovered. I'll not be sharing any of the recovered files in any identifiable form - they are, after all, not my files to share.
I'll also detail a few techniques I tested for securely erasing the cards so that the data could no longer be recovered
The Issue
Issues with erasing from storage media aren't anything new, they've been known about for decades in technical and semi-technical circles.
Amongst the average user though, there perhaps isn't the understanding that "deleted" simply means a file has been removed from view.
Within the filesystem on the storage, the reference to the file - i.e. something telling the operating system that the file exists and where to find it - as been removed, but the actual file content is still where it was. Now that the space it occupies is no longer occupied it may get overwritten when something new is written to disk (depending on what other space is also free).
How likely your file is to be overwritten depends on the size of the file (i.e. the space it's free'd up), how much storage you're using (a routinely full disk is going to lead to it being overwritten sooner) and how much use the storage gets after you've deleted.
Formatting a SD card generally simply means that references to all files have been removed. The space itself hasn't been cleared so much as made eligible for overwriting
The SD Cards
My batch of micro-SD cards - acquired via Ebay - consisted of 10 micro-SD cards.
Each was initially checked by plugging in and looking to see what was on it. All but 2 were entirely empty, with the 2 exceptions having some directory structures (but no files) visible.
All arrived formatted with either FAT or FAT32
Working from Images
To ensure that I could try and reproduce anything weird, I created images of each of the SDs
sudo dd if=/dev/sdd of=4GB.img
This creates a disk image containing a block for block copy of the SD card.
Recovery Software
I experimented with two different bits of free and open source software
- Photorec - much simpler to use, only recovers "complete" files but doesn't generally recover the original filenames. Has a curses UI
- Sleuth Kit - Much, much more advanced in operation, can recover partial files as well as complete files. Recovers directory structure and filenames. CLI only
My approach was fairly simple:
Run Photorec against a disk image, then browse into the output directory in a (graphical) file manager with file previews turned on. A quick scroll through generally gave a feel for the type of content that was in there. I didn't look into files too much, other than to occasionally try and work out why there were 100s of XML files or the like.
I noted down my assumptions/conclusions for each SD, and then later used Sleuth Kit to recover directory structure and see how that changed my assumptions. Context is an amazing thing, and finding out a parent directory's name can completely turn an assumption on its head.
Results
Readers will be unsurprised to hear that I recovered a lot of files of varying types.
There were tens of thousands of images - many of them clearly family snaps and holiday pics. Certainly something that many would feel uncomfortable passing into unknown hands.
3 of the SD cards, however, contained much more sensitive images
Sensitive Card 1
One 4GB SD card belonged to a muslim man in his early 20s back when BlackBerry Messenger was king. We can tell this because of his habit of screenshotting BBM chats.
Clearly he must have been a bit of a smooth talker because amongst the files recovered were self-taken nudes clearly sent to him by various women via BBM.
Some of them were seemingly so taken that they wrote his name, in lipstick, on their chest, though pictures weren't constrained to the top half of bodies. Clothing was also very much optional, or pulled out of the way.
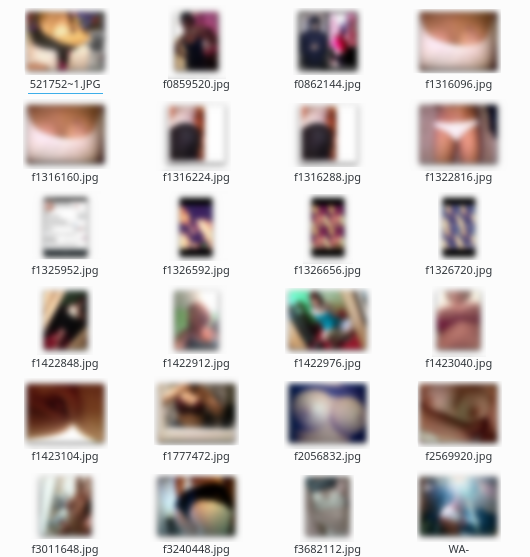
We can also tell that this user was a (relatively) early adopter of WhatsApp. The thumbnail in the bottom right corner was sent via WhatsApp, and when the image was later processed with Amateur Sleuth the WhatsApp directory heirachy was one that they haven't used in an extremely long time.
In some ways, these images being recoverable is made worse by the fact that their not images of the SD card's prior owner. The images were sent to someone in the course of chatting/flirting, but the storage they were written to then wasn't disposed of appropriately.
In the screenshot above there are also two oddly related images - f1322816.jpg is a picture of a girls crotch (in knickers). f1325952.jpg is a screenshot of the SD owner's BBM profile - he's set the profile picture to be that image, and set his personal message to "Who wants the girls number?"
Third from the left on the top is where he used mypicstory.com (anyone remember that?) to put a picture of himself next to the woman's image.
Sensitive Card 2
One of the 8GB cards started out like many of the others - lots of family snaps, often involving a couple in their mid-fourties.
There were photos strongly indicating which team they supported and that their son played in the youth team for that team, which isn't ideal.
But then other things started emerging:
- A directory full of vcards revealing a bunch of their (at the time) contacts
- Pictures of Environment Agency Licenses showing 2 different names - surname the same both times
- Screenshots of them logging into a NTL webpage - revealing their email address (corresponds with one of the names on the EA license)
- Self-taken female nudes, crotch close-ups, chest etc
- Self-taken dick pics
- Self-taken masturbation pics (male and female) - including use of toys
- Several short videos showing woman masturbating
- 2 short videos showing man masturbating
Sleuth Kit shows that the female nudes came from the Whatsapp Sent directory, whilst the male nudes were received. Presumably the couple must have spent some time apart at some point.
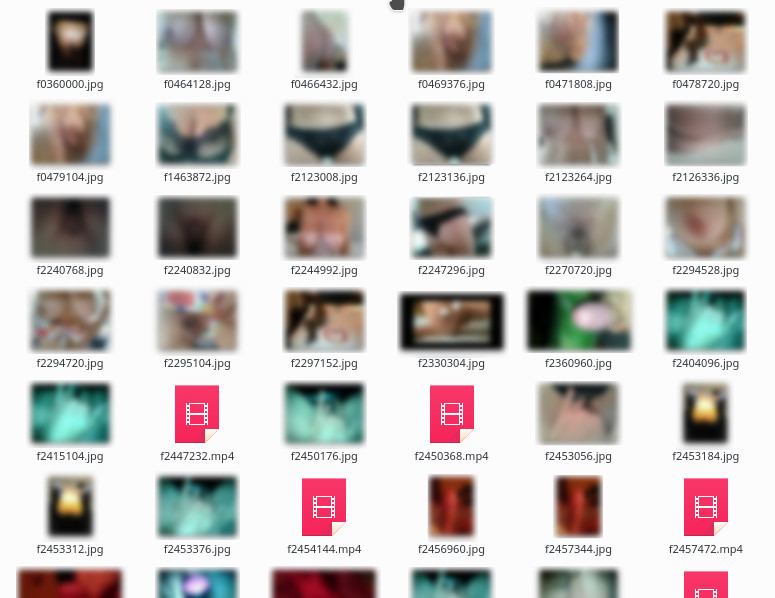
There's no mistaking that these were self-taken rather than pulled off the net - there are multiple similar photos where the woman has presumably taken a few and then sent the one she liked best.
What's most worrying here though is the potential for blackmail:
A 3 minute run of photorec on that SD card provided all the information that would be required to start making contact and threats - you've got the user's email addresses, and (albeit old) contact details for a bunch of people they had in their contacts.
Whilst I don't think anyone should be embarrassed of creating images like these, it's clearly going to be quite unsettling to receive a blackmail attempt from someone who's got hold of the images.
Sensitive SD 3
Of course, not all that's sensitive is sexual.
Another 8GB micro-SD contained sensitive financial information.
The prior owner had quite clearly applied for and taken out a fixed sum loan - amongst the files recovered were
- a PDF containing the loan agreement (including amount, his name, full address etc)
- Copies of bank statements presumably submitted in support of his application
Result Summary
photorec takes about 3 minutes to run on an 8GB SD card (depending more on how many files it has to recover and how fast the medium you're writing to is). All SD cards yielded files that the previous owner believed had been deleted, the only thing that really varied was how sensitive these files might be perceived to be.
That, of course, is itself subjective - some people will care much more about family snaps ending up in unknown hands than others. Though, I suppose it also depends on what's done with them - suddenly finding a family photo at the centre of a viral meme probably wouldn't be a particularly fun experience, even if the photo itself isn't that sensitive on the face of it.
At the more extreme end though, are cards where the contents are a blackmailers dream - content to be used in the blackmai attempt, along with a ready made list of people to threaten to contact, and contact details for your would be victims. Given that the couple's son played for a clubs youth team, there's probably a path there to figure out how much money the family might now have - at least if he stuck with it.
Blackmailers aren't the only potential profiteers here though, there's potentially plenty for identity thieves to get their teeth into to.
Although it's a small sample, 3 in 10 of the sd cards revealed information that was immediately identifiable as extremely sensitive. It's quite possible that some of the others also contained better hidden sensitive information - the sort of person interested in that data is likely to spend more time looking than I did.
Wiping Cards Properly
One of the things I wanted to do while writing this was to make sure I didn't fall into the trap of saying "look, it's perfectly simple to secure erase a card, just install this OS you don't use, or spend this money you don't have, and it's done".
So, I wanted to do some experimentation on approaches - not to mention that wiping these cards properly is the right thing to do, even if it is years too late.
Formatting the disk
Forget it.
As I mentioned in the introduction, this gives you a false sense of security because all the files appear to be gone. They remain just as recoverable no matter how many times you format it, or which device you formatted in. Even changing the filesystem makes no difference.
Linux - shred
Lets start with the option that'll fail to meet most user's needs. shred is excellent, however most users aren't running Linux. But and increasing number of users are using Apples OS X - shred is part of coreutils and can be installed on a Mac
The run was a simple
sudo shred -z /dev/sdd
Default settings means there'll be 3 passes of random data and the -z means a final pass will happen overwriting the random data with 0s
Following this, no files could be recovered from the SD with photorec, and amateur sleuth outright refused to run against it because it couldn't identify even the remnants of a filesystem on there.
Android - Enabling SD Encryption
Android supports encrypting the filesystem on SDs (more on that later), so I thought it might be possible to use that as a fairly accessible tool.
Generally when you set up an encrypted filesystem, part of the process involves writing random data across the disk/partition so that an outside observer (i.e. someone without the keys) cannot tell how much storage has been written to.
Android, it seems, disagrees. Enabling encryption on a SD card will cause files that haven't been deleted to be overwritten with encrypted versions of themselves, but it'll do absolutely nothing with space that isn't referenced - even if you subsequently go in and format the card in the hope that it'll then flush the SD with random data.
As an after the event wiping mechanism, it's useless. Files remain as recoverable as before.
A Secure Wipe App
Here's where things can quickly get messy.
Google's play store is full of apps claiming to offer secure erase. Some of them require upfront payment to download, others are free but seem to be extremely sketchy. Others are free to download, but then try and take micropayments when you use them.
However, after a bit of searching around, I found the least scammy looking option - Secure Wipe. It doesn't look particularly pretty, but otherwise seems fairly up front.
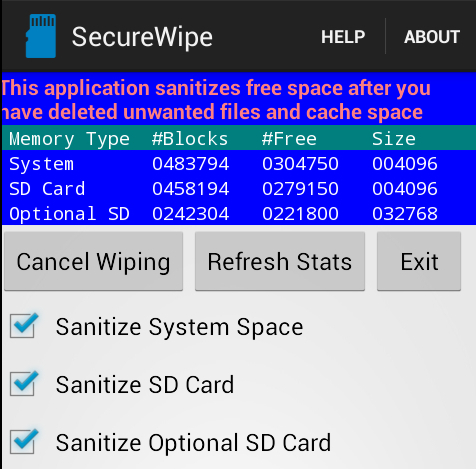
My one complaint about it would be that it follows Android's naming convention - the card you care about wiping isn't "Sanitize SD Card" but "Sanitize Optional SD Card" even though you're only aware of one card being connected in.
Following a run of this, photorec found only 4 files, none of which were historic files but new files created by the app to fill space on the SD card with random data.
However, a word of warning:
when I used this app on another SD card, I found I was still able to recover 10 files. This is because the card had been partitioned at some point, where it's original use had (presumably) been onto the unpartitioned card - the result is that there was a little bit of space at the beginning of the SD that the app isn't able to write into.
Recommendation
In summary, if you've access to a Mac or Linux box then your best course of action is to plug the card into that and use shred to wipe it. No complicated switches required
If that isn't an option, then Secure Wipe on Android achieves an acceptable level, just be aware that it may miss some amount of data in the way that you use your card has changed at a technical level.
Protecting yourself
The very best way in which you can reduce the likelihood of recovery for any future files you save to storage is to enable files-system encryption.
As noted above, it's not much use for dealing with files you've already deleted, but it provides automatic protection for anything that's not currently deleted on your SD, as well as anything new you create. Although deleting a file still won't automatically remove it, it's now an encrypted blob - theoretically indiscernible from random data - and will take much, much longer to recover if at all.
On Android enabling SD encryption is as simple as
Settings -> Security -> Encrypt External SD Card
Then follow the on-screen instructions. As much as the Police might like us to think otherwise, file system encryption isn't simply some criminal tool, it exists to help protect us against misuse of our storage.
As environmentally unsound as this next bit might be: in the event you can't use encryption, the second best thing you can do is to simply not sell SD cards on.
For the small amount of money you get for a second hand SD it's not usually worth the risk - take a hammer and chisel to it instead to ensure it's physically destroyed.
Closing Notes
There are a couple of other things to note here:
- Many phones automatically make thumbnails of media so that they can be shown in gallery views etc. What this means in practice though, is that there are multiple (albeit smaller) copies of your images being saved onto storage, increasing the probability that at least one of them will be recoverable. Essentially it gives the attacker a much wider window
- All recovery actions done in pursuit of this was done to an encrypted filesystem to ensure that I didn't end up with recoverable copies of the files on my storage, accidentally perpetuating their survival
- The files have all now been deleted
I'd be remiss if I didn't include a warning for anyone considering repeating this experiment. Be aware that you have no way of knowing in advance what you might be exposing yourself to.
One of the SD cards clearly belonged to a teenage girl, and as a result I was exposed to an unholy number of One Direction Memes. That's bad enough, but obviously it could have been much, much worse - you may well find things that you cannot unsee.
Our phones (which is where these cards have ultimately lived) are incredibly personal, and even a quick scan over thumbnails in preview mode can make you feel quite uncomfortable - it really does feel like you're encroaching. That's perhaps a good reminder that we should all be taking more care with what happens to our storage though.
