Will Anonymity ever be impossible on the Internet?
We all value our privacy, with many seeking to remain anonymous. We're told time and time again that development of interception technologies, with increasing government oversight mean that anonymity on the internet will soon be a thing of the past.
Is this true though? Are we moving towards a day when everything we do online will be monitored and scrutinised by government agencies?
Some may be aware of my support for Freedom4All, for whom I've lent a lot of support. I designed, at the request of the Freedom4All Admin Team, a system for ensuring their anonymity whilst they access, run and manage Freedom4All.
Whilst I'll obviously not be divulging too much information, I'll provide a basic explanation of how the system works, and examine what future risks may lay instore.
We'll also be taking a quick look at the current privacy threat – commercial organisations.
Freedom4All PrivNet
The Freedom4All privacy system (known as PrivNet and AnonNet) had the following requirements;
- Had to offer maximum privacy protection
- Could require no special software on the client
So, a vague description of the process would be as follows;
The user connects a Pay as You Go mobile phone to their PC/Laptop and uses it to dial to the Pay as You Go mobile situated at Benscomputer.no-ip.org. This is connected to a dedicated dial-up gateway and once comms are established the PC/Laptop connects to our dedicated VPN.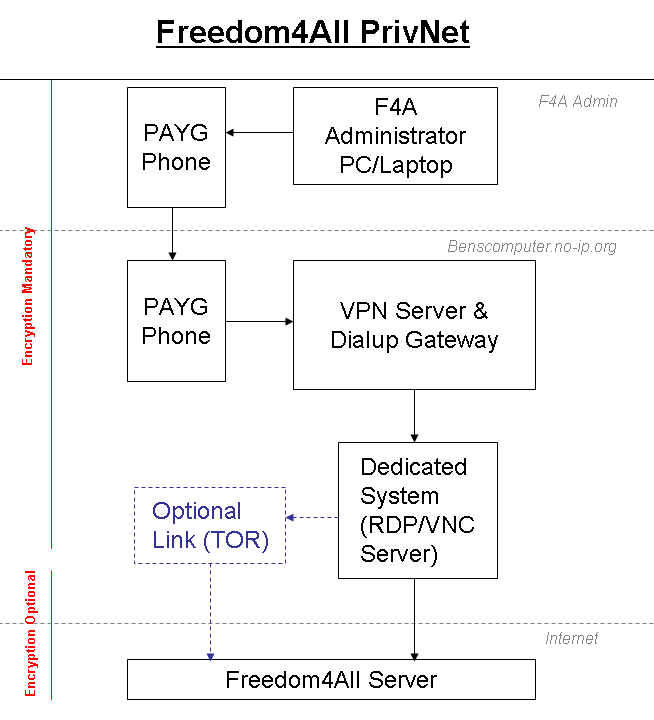
The user then uses VNC or RDP to connect to a dedicated machine. They then use the browser on this machine to update Freedom4All. As an added level of protection, we can also route their connection through TOR.
This means that even if a Government/Company were to demand access logs from Freedom4All's webhost, all admin connections would come from Benscomputer.no-ip.org. Unsurprisingly, PrivNet keeps no logs whatsoever, so even a raid on our premises would yield nothing to establish the user's identity. Both PAYG phones are unregistered, and the VPN ensures that all data is encrypted when passing through the mobile network.
We utilise Pay As You Go mobiles so that the numbers can be changed easily and when necessary. Because the user dials into the system directly, interception of the Benscomputer.no-ip.org internet connection would not reveal any incoming connections.
My name is registered against the Freedom4All website, and I act as a proxy for any donations received via PayPal.
I'm personally pretty confident that PrivNet should be more than sufficient to protect the privacy of the Freedom4All administrators. I don't know their true identities which also means that I cannot accidentally leak the data! We also have more than one PAYG phone deployed, with each Admin holding more than one.
The Future
The system isn't watertight, if it were encryption we'd call it computationally secure rather than cryptographically secure. It is possible to breach the system, but the steps necessary should act as a deterrent to all but the most determined. The only parties able to take such steps would be Governments. The problem is, Freedom4All's work does carry the risk of upsetting Governments.
So let's examine the areas of the system that could be attacked by a very determined attacker;
- If the attacker knows the IMEI of either PAYG mobile, they can locate the phone and/or identify the number being used.
- The attacker could triangulate the admin's phones and locate them directly
- The attacker could identify the number of the phone at Benscomputer.no-ip.org and contact the operator to obtain details of all calls to the phone
- The attacker could try and compromise the systems at Benscomputer.no-ip.org in order to intercept all network traffic.
- The attacker could install a 'wiretap' to monitor connections to the Freedom4All server (would not automatically lead to the admin's identity, however)
We already take some steps to mitigate some of these risks, the use of unregistered PAYG mobile phones means that we can change our numbers at the drop of a hat. Obviously, if we change the number of the phone at Benscomputer.no-ip.org we need to notify them of the change (a method exists, but won't be disclosed for obvious reasons!).
There's very little we can do to mitigate risk 2, but it's also very easy for us to change the hardware. Most modern phones can be used as dial-up adaptors, and with Carphone Warehouse selling phones from as little as 99p there's very little cost in changing.
Risk 3 is partially mitigated in that the attacker would need to be able to show reasonable cause, and even if they could, both phones are unregistered so they couldn't directly obtain the names of the Freedom4All Admins.
We've mitigated risk 4 by ensuring that all public facing servers are kept separate from the PrivNet hardware. We use a switched network, so packets never actually pass under the nose of the few bits of hardware that could be compromised. This prevents an attacker from deploying a packet sniffer, and as the potentially vulnerable hardware is firewalled from the rest of the network, it can't even be used as a basepoint for an attack (or not easily at least).
We also have the capability to configure multiple VPN's on the network, ensuring that almost all network comms are encrypted.
Risk 5 is more difficult to mitigate, the Admins can connect to the Freedom4All server using SSL but a Man-In-The-Middle (MITM) attack could be used to compromise the encryption. A similar problem exists with using the TOR network. There's very little we can do to mitigate this, but if it was believed to be an issue we could configure a remote VPN server and route all connections to this.
Commercial Snooping
 It's an often reported fact that commercial organisations are collecting ever increasing amounts of data about how we use the Internet. The biggest culprit for this is almost certainly Google, this can pose a problem for PrivNet;
It's an often reported fact that commercial organisations are collecting ever increasing amounts of data about how we use the Internet. The biggest culprit for this is almost certainly Google, this can pose a problem for PrivNet;
The Admin's occasionally use PrivNet in order to conduct research. This helps them avoid privacy invasions in that they are able to access any website without disclosing their true identities. It's a well known fact that Google collate details of all your searches, over time this data can often be used to identify the (otherwise anonymous) user. Whilst the RDP/VNC system is configured to automatically delete all private data upon log-off, a single long research session could potentially be sufficient to identify a user.
Commercial snooping operations evolve far more quickly than those of Governments and other organisations, and therefore pose the most prominent threat to the integrity of PrivNet. As new techniques emerge (especially within the area of 'Behavioural Advertising') the system will need to be honed and updated in order to ensure maximum privacy is maintained.
Self Defence
Now the truly paranoid would be asking an obvious question - What if the Freedom4All Admin's aren't as honest as one would hope? What I'm allowing them to do is to access the net using a connection in my name, with no logs to prove that it wasn't me that accessed anything they may choose to load.
As it happens, I've chosen to trust the Freedom4All Admins, but when I designed PrivNet I did consider the need to restrict their activities on PrivNet. In order to do so, I have a SQUID proxy configured with a 'walled garden'. If I chose to force the RDP/VPN system to connect through this proxy, I can limit which sites and services can be accessed. I can institute this control at the touch of a button, even if the F4A Admin's are in the middle of a session.
As you'd imagine, logging is also disabled on the SQUID proxy.
When designing PrivNet I discussed their needs with the F4A Admins, there's very few services that they actually need to access through PrivNet. Whilst I've not limited their web (read port 80) access, they are unable to use Peer to Peer software (for example).
Conclusion
Although I'm not infallible, I believe that it would be difficult to create a system that protects privacy better than PrivNet. There are some small holes, and the system will need to evolve to keep pace with commercial interests but it serves to protect the privacy of the Freedom4All Administrators.
Given the relative ease with which PrivNet was conceived and built, I think it's highly unlikely that Internet Anonymity will ever truly disappear. Commercial organisations and Governments alike would love to be able to track our every activity online (as the Interception Modernisation Project highlights), but it'll never be possible for either group to keep everyone from achieving anonymity. It may, eventually, become too difficult for the average user, but there will always be those willing to find new ways.
So long as these people continue to seek out anonymity, there will always be someone willing to help ordinary users to find anonymity.
